By Mario Rojas, Senior Security Researcher
In previous posts, we explored how to build and customise a Google Custom Search Engine (CSE) to streamline vulnerability research. Now, we’ll take things further by enriching CSE results with additional intelligence sources.
When tracking CVEs, simply finding a mention in a security blog or forum isn’t enough. To assess risk effectively, you need more details:
- What’s the severity and impact of this vulnerability?
- Is there a known exploit or proof-of-concept (PoC) code?
- Is this CVE actively being used in attacks?
- Which Threat Actors are targeting this CVE?
By automating enrichment, we can take search results from a basic list of links to actionable intelligence, helping security teams prioritise threats efficiently.
Step 1: Extracting CVEs from Google CSE Results
Google CSE is an excellent way to discover CVE mentions across security blogs, research reports, and exploit discussions. But first, we need to extract the CVE identifiers from our search results.
Fetching CVE-Related Results:
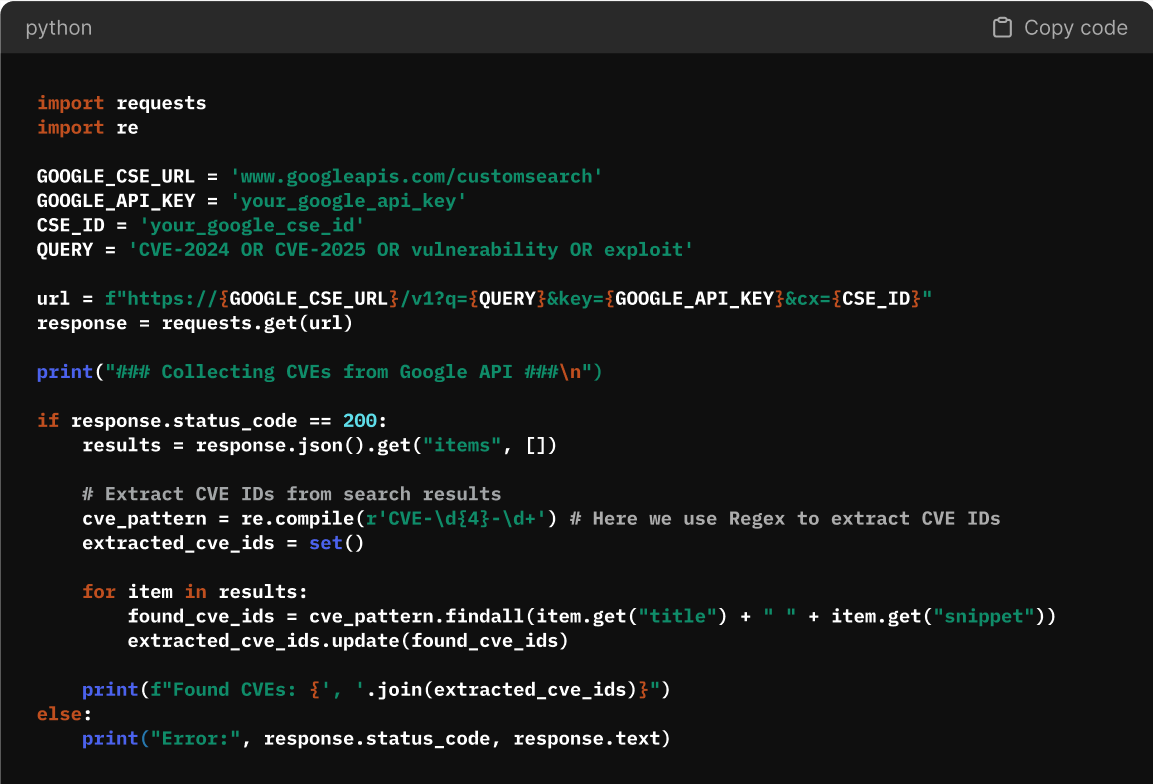
You should get something like this after running your script:

What This Does:
- Queries CSE for vulnerability-related content.
- Extracts CVE identifiers (e.g., CVE-2025-1094) from search results.
- Returns a list of CVEs found in blog posts, forums, or advisories.
At this point, we have a list of CVEs mentioned in various sources. Next, we’ll enrich them with official data from the National Vulnerability Database (NVD).
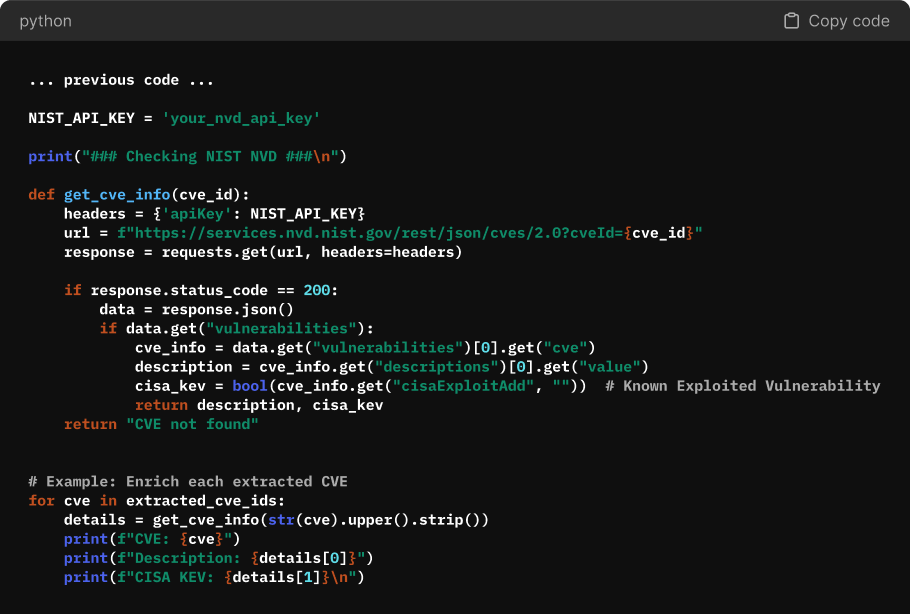
Step 2: Enriching CVEs with NVD Data
Once we have a list of CVEs, the next step is pulling official details from the National Vulnerability Database (NVD). This allows us to access:
- Severity ratings (CVSS scores)
- Affected vendors and products
- Exploitability and patch availability
To query NVD, we can use their API which allows structured searches for vulnerability details.
Fetching CVE Details from NVD
You should get something like this after running your script:
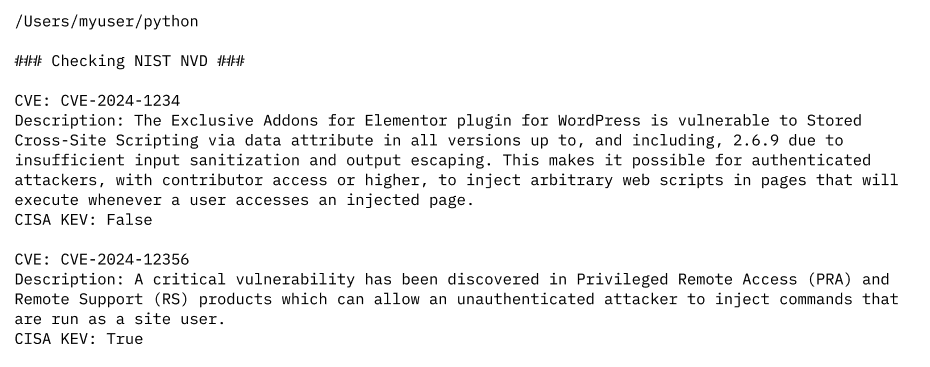
Why This Matters:
- Provides official descriptions from MITRE/NIST.
- Confirms if a CVE is valid (or still in draft status).
- Includes additional information like CISA KEV status.
To get higher request limits and additional API features, you can request an API key here. This ensures faster responses and better access control for large-scale queries.
Step 3: Checking for Public Exploits with Nuclei Templates
Understanding whether a CVE has a proof-of-concept (PoC) test or known exploitability is critical for risk assessment and prioritisation. While not every vulnerability has a working exploit, security researchers and red teams frequently develop scanning templates to verify whether a system is vulnerable.
Nuclei is an open-source vulnerability scanning tool that maintains CVE-specific templates. These templates provide a structured way to test for known vulnerabilities without relying on unreliable or rate-limited exploit repositories.
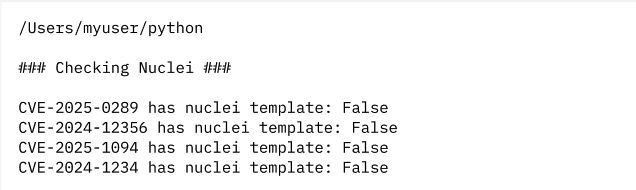
Checking Nuclei for CVE Templates
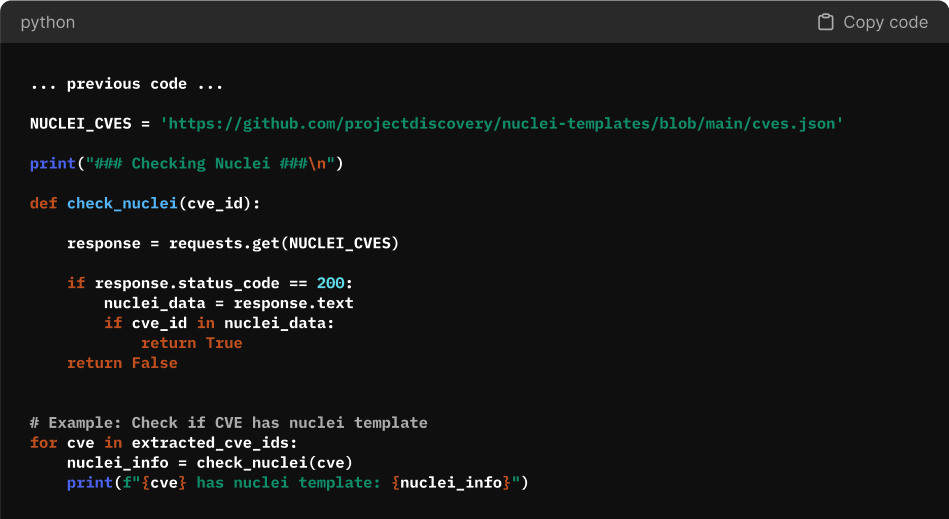
You should get something like this after running your script:
Why This Matters:
- Identifies vulnerabilities with publicly available security tests.
- Allows security teams to verify exploitability in real-world environments.
- Supports automation by integrating with vulnerability scanning workflows.
By checking for Nuclei templates, security teams can quickly determine whether a CVE has known detection or exploitation methods, making it easier to prioritise remediation or conduct further testing in a controlled environment.
Step 4: Identifying Threat Actor Associations
Not all CVEs are the same: while some remain theoretical risks, others are actively exploited by threat actors in real-world attacks. Identifying which vulnerabilities are linked to known adversaries can help security teams prioritise patching efforts and assess the urgency of a CVE.
To determine whether a CVE is part of an active attack campaign, we can cross-check it against threat intelligence feeds such as AlienVault OTX, a community-driven threat intelligence platform that tracks IOCs, vulnerabilities, and adversary behavior. You can request an API key here.
Checking AlienVault OTX for Threat Intel
You should get something like this after running your script:
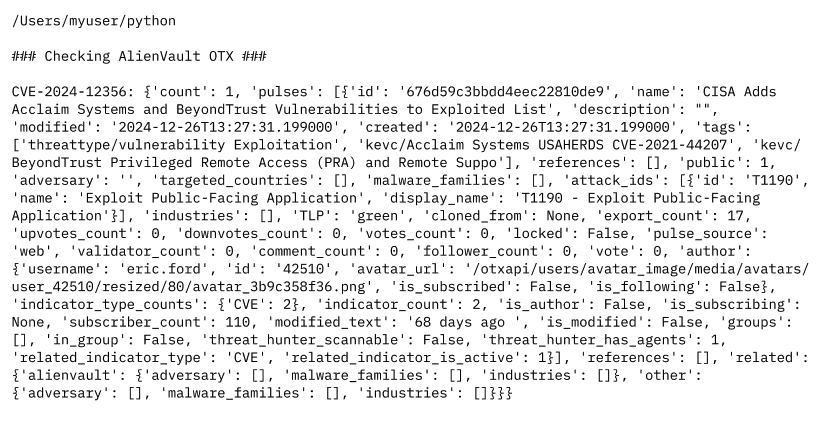
Why This Matters:
- Detects if a CVE is part of an active attack campaign.
- Identifies threat actors and malware using the CVE.
- Helps security teams prioritise patching efforts.
Once you put everything together you should get a nice formatted summary like the one below.
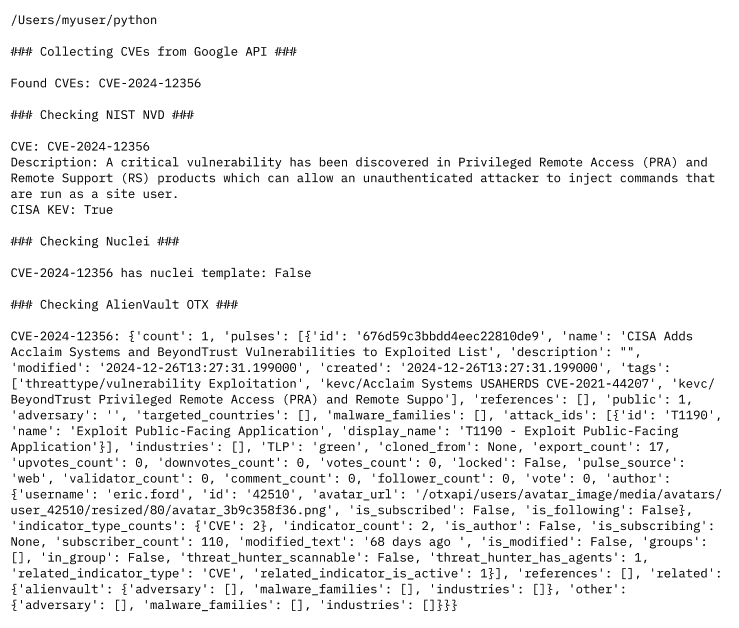
Conclusion
This post marks the final entry in our Google Custom Search Engine (CSE) for OSINT series, and we hope it has provided you with valuable insights into building, customising, automating, and enriching your CSE for more effective intelligence gathering.
By applying CVE enrichment techniques, you can transform basic search results into actionable intelligence, helping security teams assess risks faster, track exploitation, and prioritise vulnerabilities based on real-world threats.
Throughout this series, we covered:
The goal of this series was to help OSINT practitioners, threat intelligence teams, and cybersecurity researchers get more from their searches. By leveraging Google CSE as a powerful intelligence-gathering tool, you can streamline your workflow and stay ahead of emerging threats.
Thank You!
We appreciate everyone who followed this series, shared feedback, and explored these techniques alongside us. OSINT is a constantly evolving field, and the best tools are those we refine and improve over time.
This may be the end of this series, but the OSINT journey never stops. Keep exploring, refining, and optimising – there’s always more intelligence to uncover.
